Overview
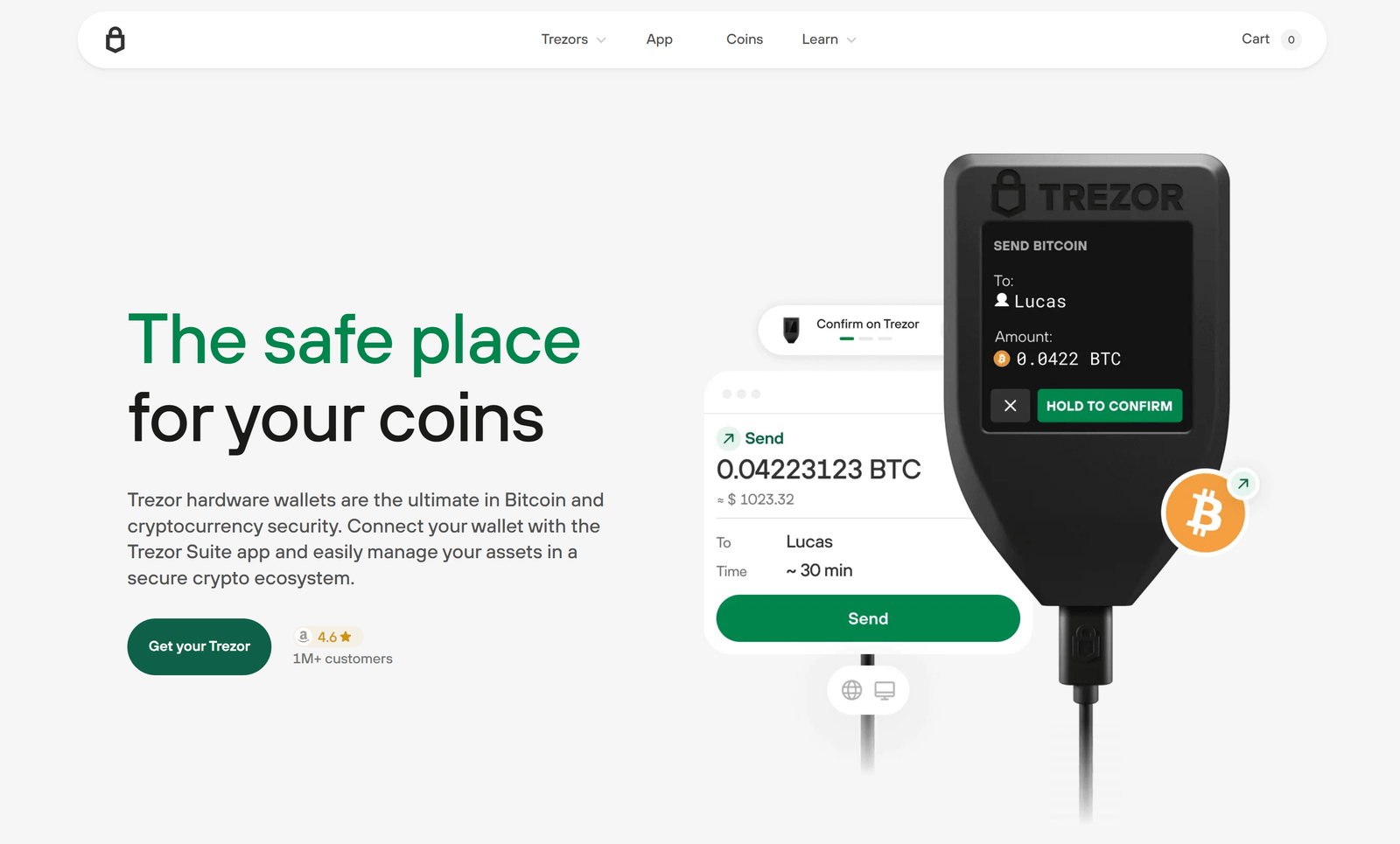
Trezor Login enables users to access their cryptocurrency wallets securely through the Trezor Suite platform. It uses hardware-based authentication, ensuring that all approvals are confirmed directly on your Trezor device screen—keeping private keys fully offline and protected.
This process replaces traditional password logins with device-level confirmation, removing the risk of phishing or credential theft.
How Trezor Login Works
- Connect your Trezor hardware wallet to your computer using the USB cable.
- Launch Trezor Suite and select your connected device.
- Confirm the login request on your Trezor device’s secure display.
- Access your dashboard to view balances, manage crypto assets, and send transactions.
Every login request must be verified on your Trezor device—this ensures full protection even if your computer is compromised.
Security Features
- All credentials remain stored within the hardware wallet’s secure chip.
- No passwords or sensitive data ever leave the device.
- Every login request requires physical confirmation on your Trezor screen.
- Protection against phishing, malware, and remote attacks.
Troubleshooting Login Issues
- Device not detected: Reconnect the device and ensure Trezor Bridge or Suite is installed.
- Blank screen: Use an official cable and restart the device.
- Browser not connecting: Close other crypto applications that may interfere with USB communication.
- Stuck on “Waiting for confirmation”: Check your Trezor device screen to approve or deny the request.
Frequently Asked Questions
Q1: What is Trezor Login?
A: It’s a secure authentication process using your Trezor hardware wallet to verify your identity within Trezor Suite.
Q2: Is an internet connection required?
A: Yes, but your private keys never leave the Trezor device even while online.
Q3: Can I log in without my Trezor device?
A: No. The hardware wallet is essential for authentication and transaction approval.
Q4: Why do I need to confirm on the device screen?
A: It ensures that even if your computer is compromised, no unauthorized action can occur without your approval.
Q5: How often should I update Trezor Suite?
A: Always keep Trezor Suite and your device firmware updated for the latest security improvements.
Q6: Can I use Trezor Login on multiple computers?
A: Yes. You can connect your Trezor device to any trusted computer running Trezor Suite securely.